Posted in Uncategorized
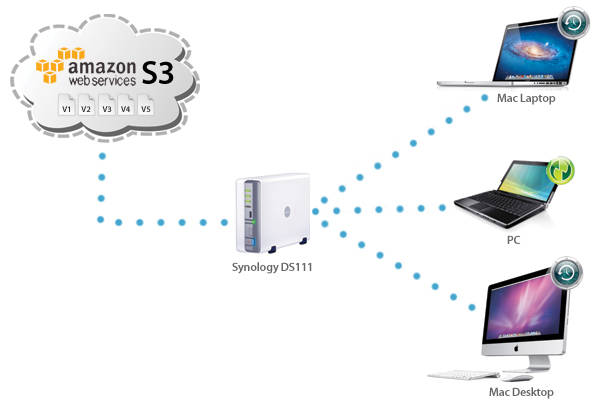
Most data-driven modern enterprises have gone to great technical and monetary lengths to create a semblance of security for the physical and logical systems and assets. Short of disconnecting the WAN Internet connection and building an impenetrable fortress around every corporate system, there will likely always be vulnerabilities and exploits those malicious actors can and